For Halloween this year I will be telling a very chilling story of an old infected virtual machine that contracted something mysterious. The machine was a standard Virtual Box machine image that was given 20 GB of hard disk space and about 2 GB of RAM and was mainly set out for doing research into botnet malware and dark web protocols such as Tor. The Linux distribution in use was called CrunchBang (now defunct), and it was setup as a fully encrypted machine with some extra hardening of configuration files. Main parts of the study was to download botnet source code to reverse engineer, and access various hacker sites both on the clear net and dark web. However something huge was overlooked, the Tor Browser Bundle by default enabled JavaScript and so all the research to these hacking forums and other seedy sites was completely open to JavaScript attacks. However that shouldn't be much of a problem considering everything was kept up to date, and it was a Linux machine which are really hard to infect.
The Dialog Window
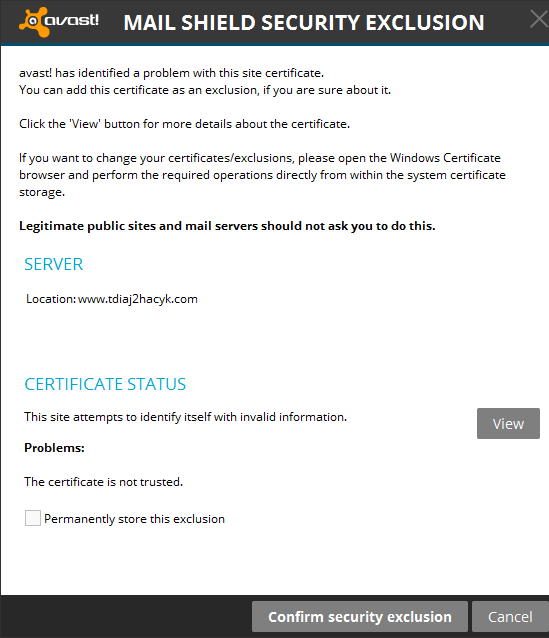
I noticed I was getting this weird dialog regularly, and since I had so much other things going on in my life I chose to ignore it, thinking it was my mail client. I would close out of it immediately so I would never actually take the time to read what was on the page. However after I had moved houses, I realized that it wasn't a routine thing, and it seemed to only start when the virtual machine would be started up...
Realization
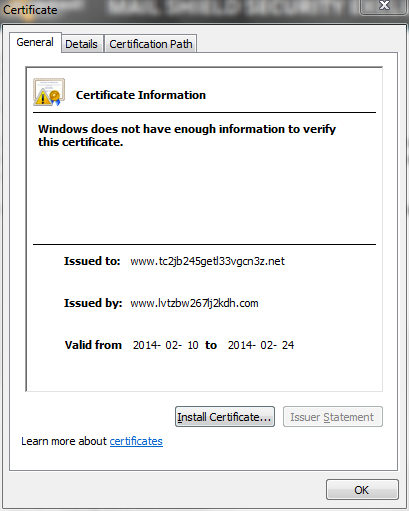
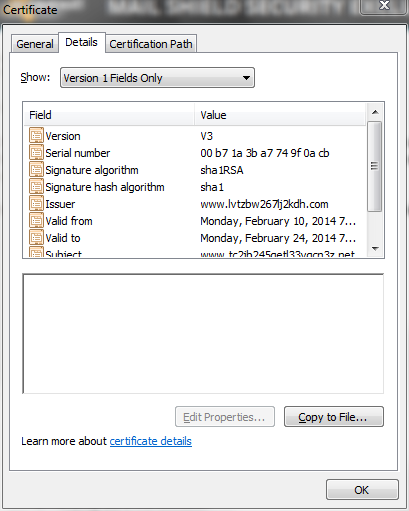
I then purposefully brought up the machine and correlating whether the dialog came up too, and my predictions were correct, it was completely correlated with coming up on each startup of the machine. The reason I never really put it all together, was because it doesn't do it every time the machine powers on. However I realized that I had a possible security breach of what was at the time an secret project and I must tread carefully with my next steps. I then clicked the "View" button on the dialog box to get a closer look of what exactly was happening.
 |
 |
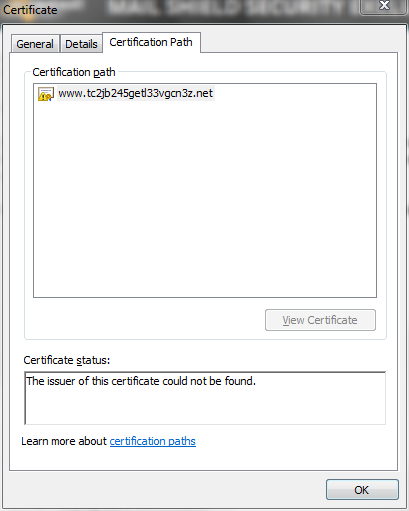 |
As you can clearly see, these domains are complete gibberish so my worse thoughts were confirmed. I had a secured virtual machine with secret company research that was infected... And trying to phone home.
Red alert
I had lost track of when I first started getting these dialogs, all I was thinking was "how in the world did this get in here". I then checked my Tor Browser and I saw I never clicked the NoScript button to enable the protection, which then lead to me thinking it was a JavaScript drive by from a forum I visited. I then set out on scouring every inch of this machine for clues as to where the infection lived, but there was absolutely no trace of it. It was a ghost within the system, a completely invisible virus, not even detected by ClamAV (an anti-virus program for Linux). I was in the simplest sense, completely pwned. However I had one hope which was the fact that I never authorized any of the connections, Avast was blocking them all because of the invalid certificate. This program probably could not connect back to it's command and control server, so my data was still probably safe. I decided it was the best thing to destroy the machine by wiping the image file, there was no way I could risk attempting to migrate the data out with an infection that is this stealthy. I thoroughly wiped the virtual disk image using a tool I can no longer remember the name of, but the machine and all the encrypted data were gone for good.
Aftermath
After scanning my host machine thoroughly for viruses, and having my server monitor it's traffic for a couple days of use, I was able to make sure that there was no infection left after the machine was destroyed. All my other virtual images I used for recreational purposes, were fine as well. I decided since I had taken screenshots of everything, it would be good to look into who attempted to steal my research or whether that was their actual intention. I looked up all the domain names within those previous screenshots and found absolutely nothing. DNS has records of everything, and there are databases of historical DNS and WHOIS records as well, so it would be impossible that it tried connecting to these domains if they weren't going to resolve. If the hacker even registered it for a brief period of time, there would be a record of it somewhere, however all these domains were completely non-existent. They had never in the history of the internet been registered, which was very odd. I forget about everything until a couple months later I was fiddling around with the features in Avast, and found the statistics of the infections it's stopped as well as files and HTTP requests it's filtered for up to a year back in time.
Patterns in the picture
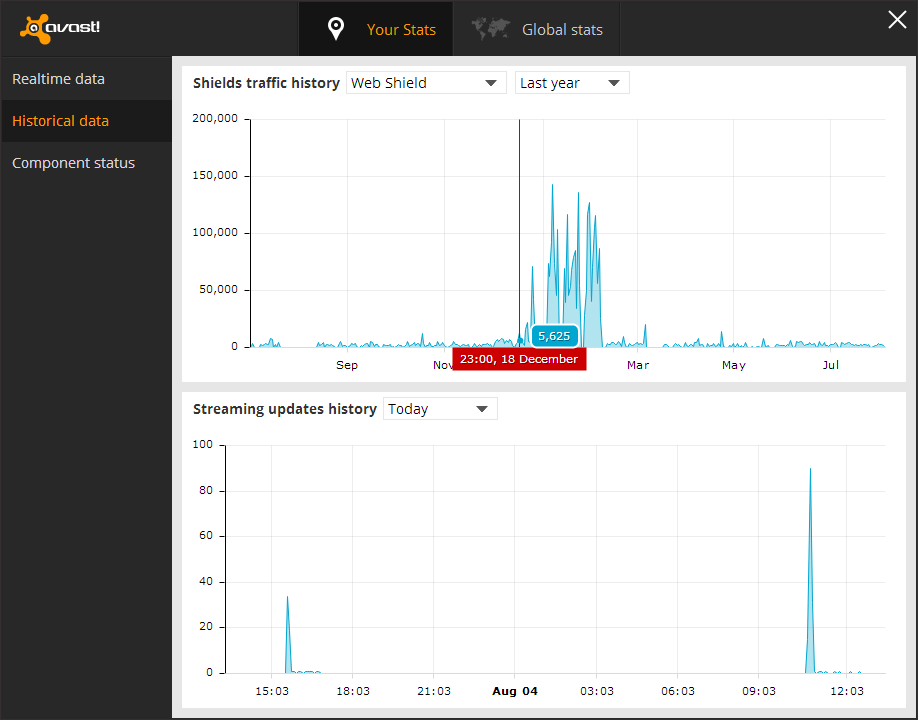
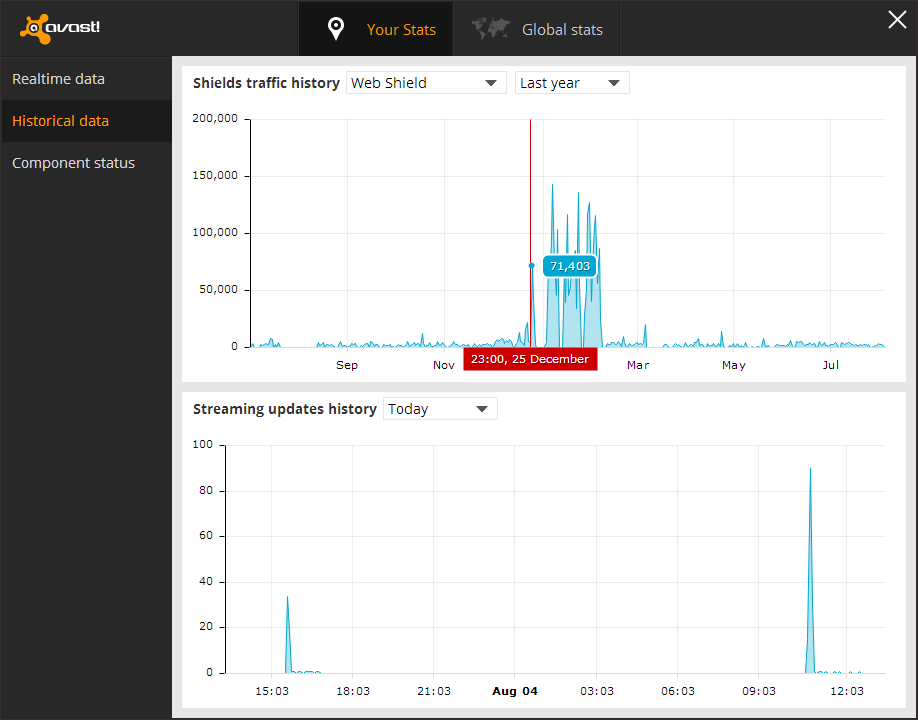
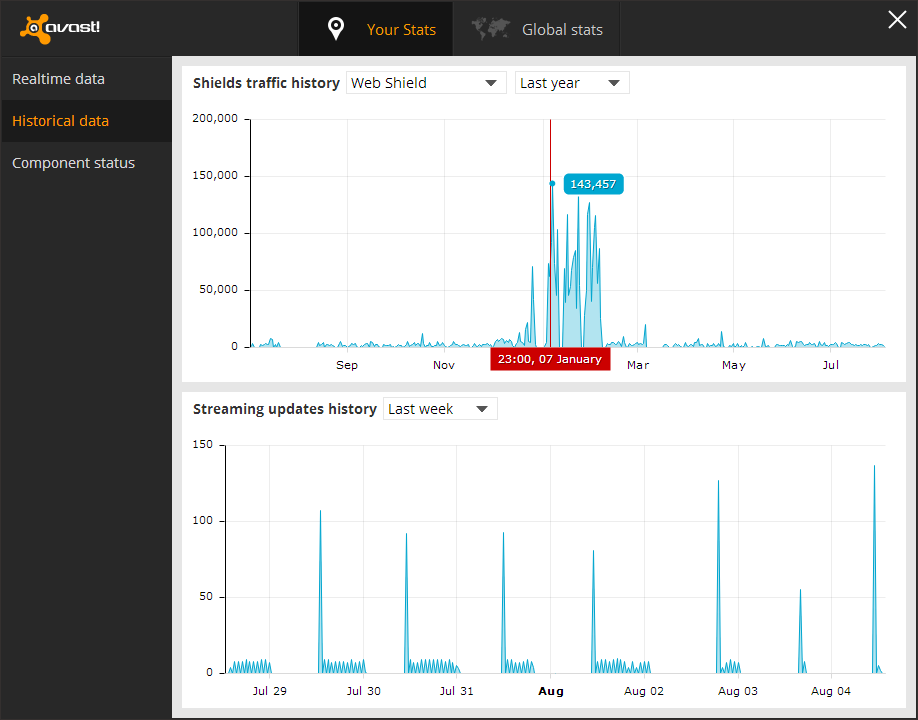
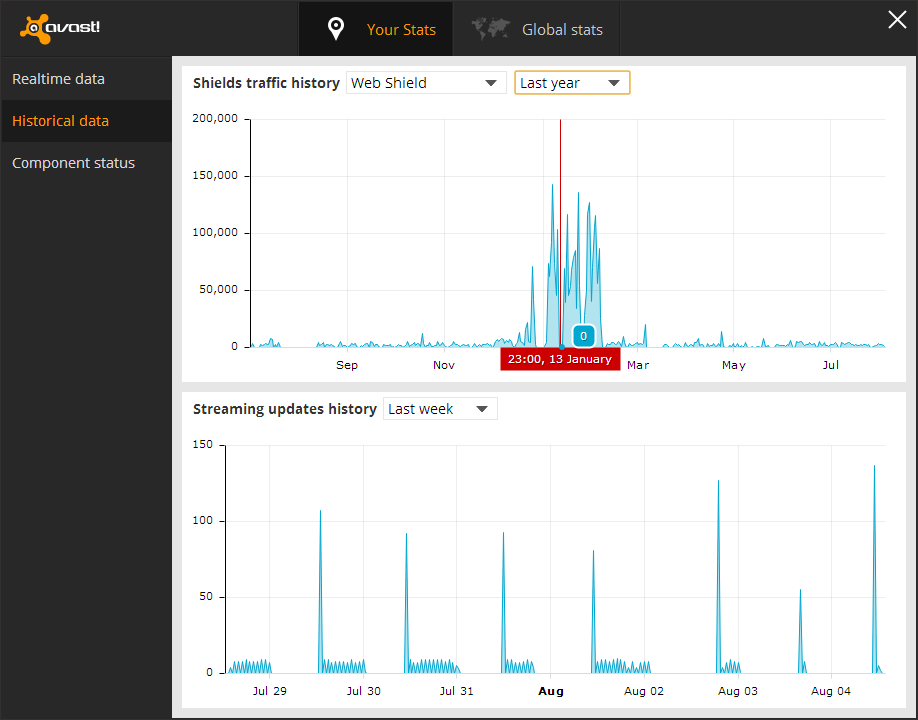
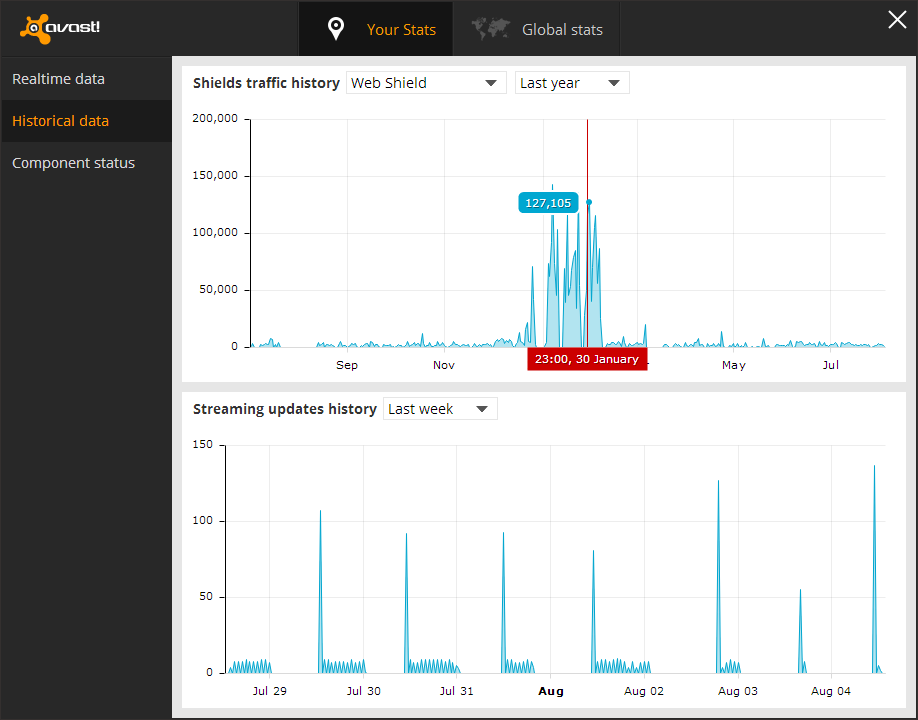
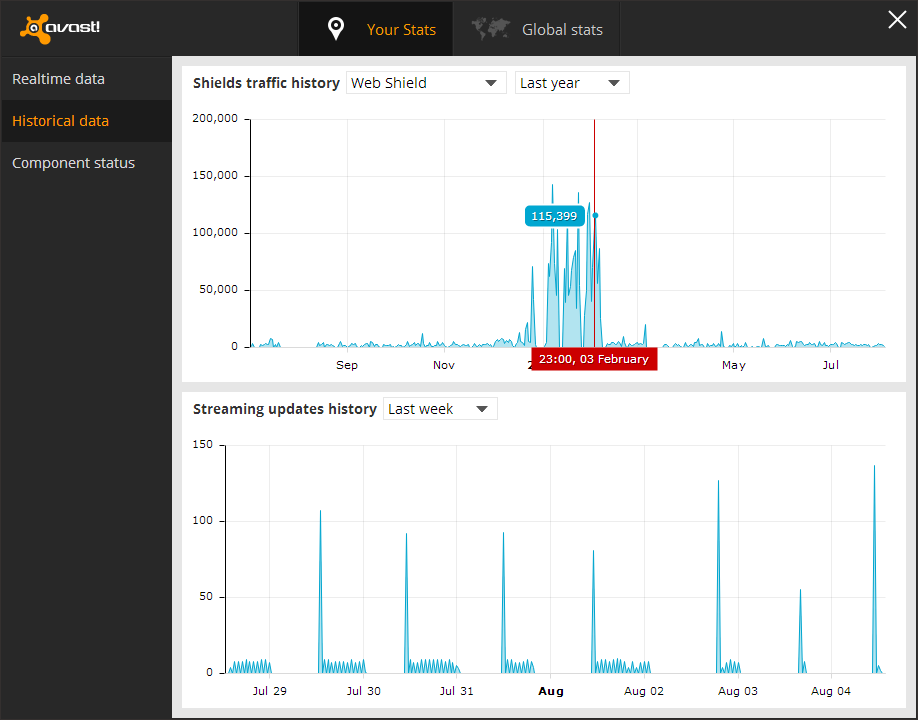
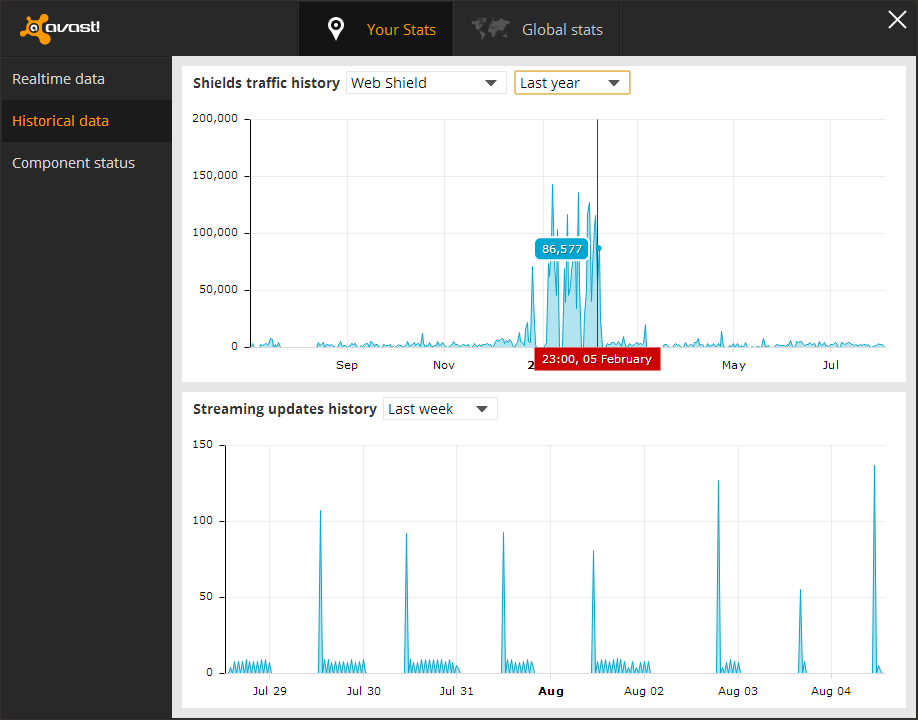
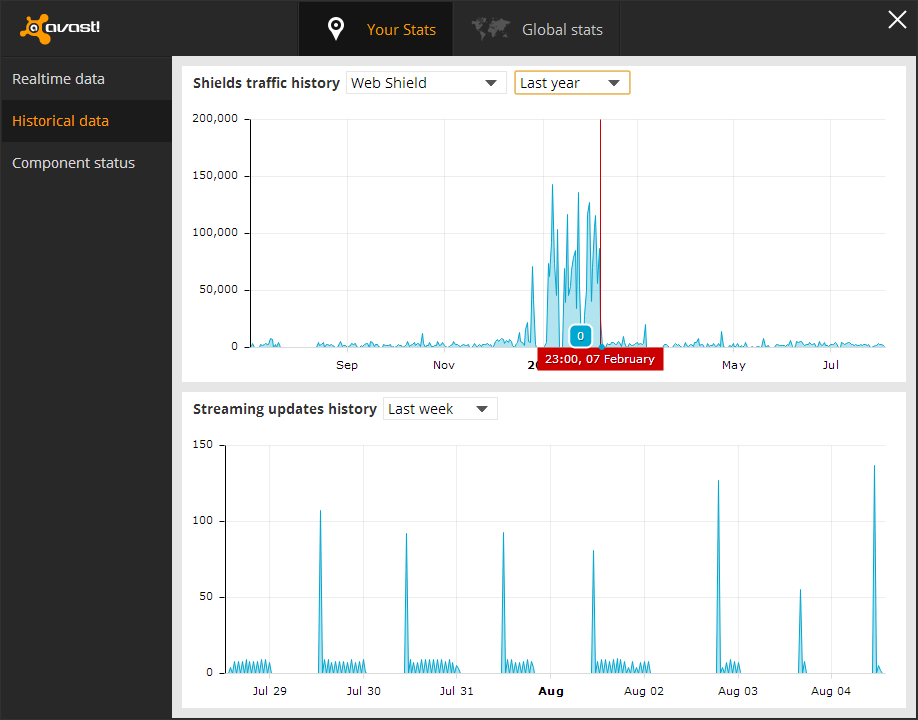
I was looking through the graphs and found the web scanner, and it had data from over a year before, so I decided to see the graph for it. I found that there was an obvious pattern that showed when the machine was infected to the day it was deleted, as well as some other information that convinced me these statistics were accurate.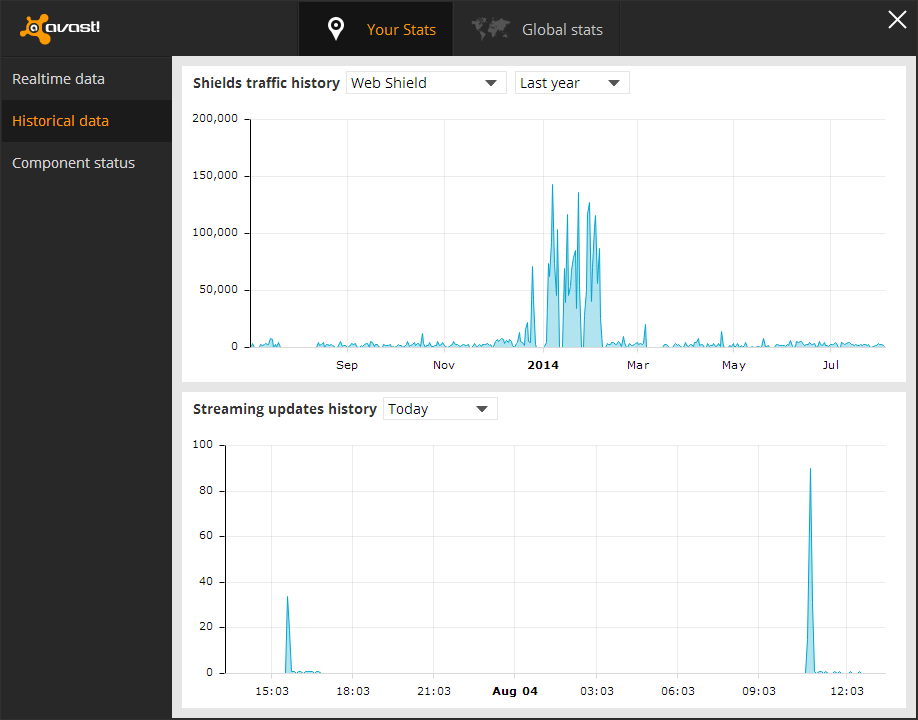
The spike in this picture is what first caught my attention, this was right when I had the dialogs come up, and then found out my machine was infected at the end of February. Also the little quite zone of activity near the beginning spike is when I moved, there was no internet installed at the new house yet so obviously the web scanner was not being utilized during that time. I realized that I didn't have the infection long before the move but it was persistent until after I got situated. I then saw the machine would send out huge requests mostly on the weekend and be almost completely quite on other days, and I realized it was from when I had time to start up the virtual machine. This was the traffic patterns of the virus infection coming back to haunt me 3 months after its deletion.
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
My theories
NSA attack
The NSA has been known to attack security conscious individuals, and even worse they specifically targeted research groups as a target of interest. My use of the Tor network probably flagged me for investigation, and using a project code named EGOTISITCALGIRAFFE attacked the vulnerable Tor browser. Also there is another program called QUANTUMINSERT which acts as a man-on-the-side attacking server to serve malware to users. However it could be used in this situation to detect the infected virtual machine, then serve resolutions to the DNS request as output by the machine. This would result in a private DNS server which serves out results for bogus names like the ones seen above. This would be particularly beneficial because the DNS system is tightly recorded, there is WHOIS data tied to every domain registrant so this would cause a problem if they're attempting to keep this from being traced back to them. In essence the benefits are three-fold:
- Prevention of hard coding NSA server IP within the program by using non-existent domain names instead.
- Removal of any link to them to the domains, which makes it harder to prove it was the NSA as opposed to another adversary.
- Containment of the sensitive information of IPs to computers which they have control over, which is recognized by "tags" sent out in traffic from an infected machine.
Forum board attack
Another possibility is that a hacker from one of the various boards either own the board and was looking for people who didn't secure their browsers well enough to be exploited. Or someone who found a vulnerability within the forum itself and used it as a platform for infecting others as well. Hackers have many motives to infect computers, however infecting a hardened Linux machine is neither lucrative nor easy. Also this theory does not explain the ability to resolve non-existent domains like the other does so it is doesn't explain everything.
Lessons learned
First and foremost run the Tor browser with JavaScript disabled. It would have probably prevented the infection in the first place if I had just clicked the enable NoScript button. Another thing that should be remembered was that it is usually not good practice to have a virtual machine with sensitive data as the host machine could possibly compromise it, however in this case it was the only thing that saved the data from falling in the wrong hands with the connection prompt. A third point that can be made is that encryption of the disk is only good for when the machine is powered off. It doesn't protect against any viruses as they have access to the active machine with the plaintext data in memory, so that must be accounted for also. One final thing is that sometimes your data might be left intact and not stolen. but you might end up having it tainted by an attack like this one, so remember to backup.